Every sniper bot shares one objective: capture early entries at favorable prices while avoiding trap tokens. Yet each missed fill and every extra 30–50ms on Solana translates directly to reduced profits. Elite systems optimize end-to-end from signal detection through final confirmation, tune fee structures based on real-time slot congestion, validate pool liquidity and token permissions, and then bail immediately when red flags appear. Amateur setups spam transactions, ignore mempool realities, skip crucial safety checks, and burn their edge through sloppy retry patterns.
Organizations run sniper infrastructure to address three core challenges:
Success means achieving sub-100ms transaction submission, landing consistently in the first 10 confirmations for target slots, and demonstrably reducing both transaction failure rates and capital loss incidents. This guide covers foundational concepts and advanced considerations for organizations deploying production sniper systems on Solana.
Rather than listing bot names randomly, we organize community-validated options by the factors that actually determine performance: network path optimization, priority fee algorithms, strategic flexibility, and pre-trade validation depth. Match these capabilities to your operational constraints, risk tolerance, and speed requirements.
The Solana trading ecosystem has matured significantly. Fee market mechanics, MEV protection infrastructure, and competitive bot density have all shifted. Priority fee handling and bundle submission paths now follow established patterns, baseline retail bot performance has accelerated, and institutional trading desks approach sniper infrastructure as integrated components of high-frequency trading stacks rather than experimental side projects.
This analysis maintains core operational principles while incorporating 2026-specific factors: stricter latency service level objectives, bundle-conscious transaction routing, enhanced risk management frameworks, and operational procedures for teams running coordinated sniper deployments across multiple blockchain networks.
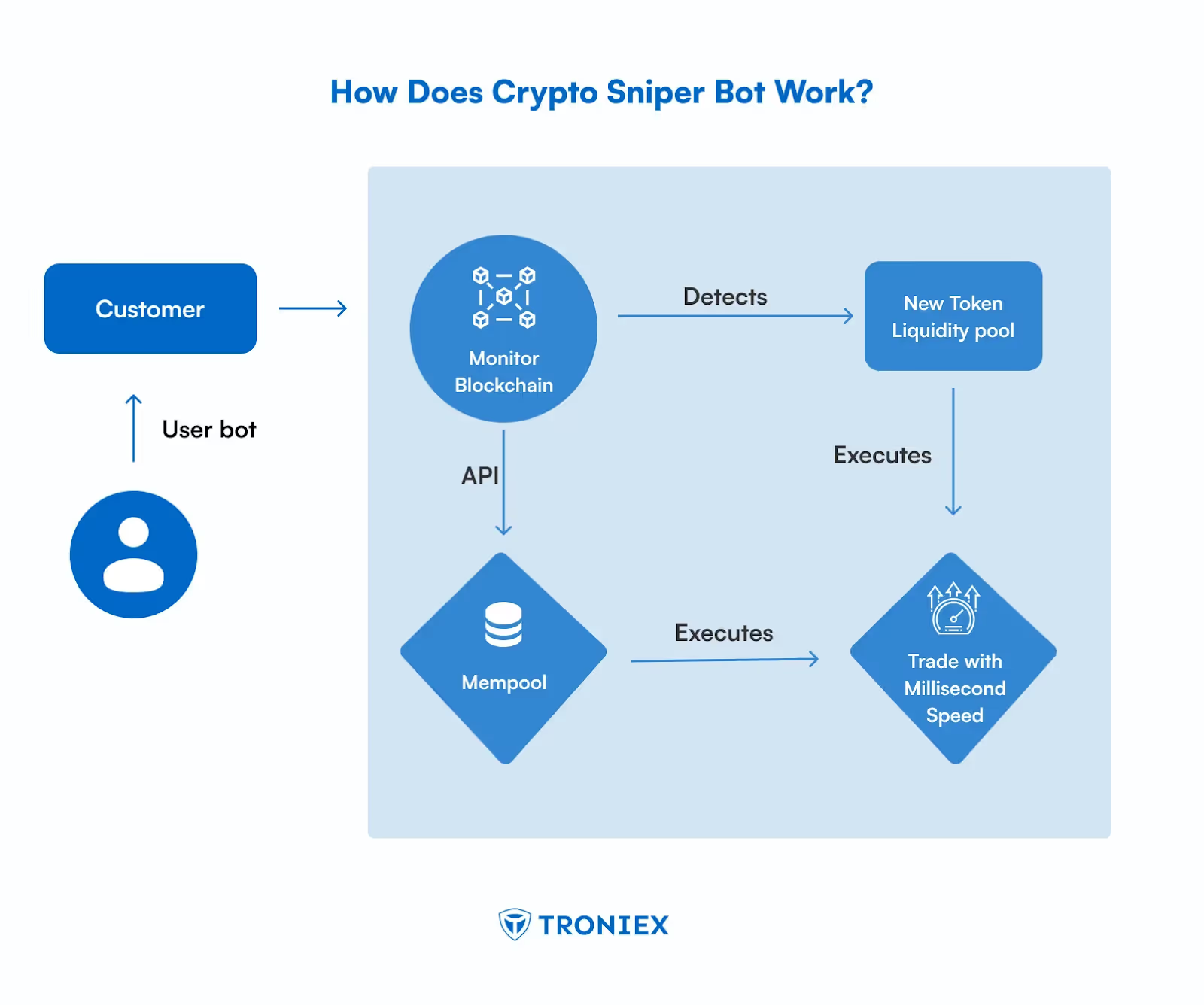
Solana sniper bots are automated trading systems monitoring token launch events and blockchain signals, submitting purchase transactions during initial available slots to capture early price action while maintaining slippage constraints and risk boundaries. The execution cycle demands precision: detect opportunity, validate pricing, route with appropriate priority fees, secure early confirmation, exit on warning signals.
Warning signals represent any indicators increasing loss probability or invalidating the entry rationale:
On Solana, competitive advantage derives from slot timing precision, understanding local fee dynamics, and RPC connection latency; misconfigured bots either spam the network or achieve late confirmations, driving up rejection rates and degrading fill quality. Professional implementations incorporate pre-execution liquidity verification, token authority validation, congestion-responsive fee algorithms, and post-trade monitoring to avoid honeypots on permissionless trading pairs.
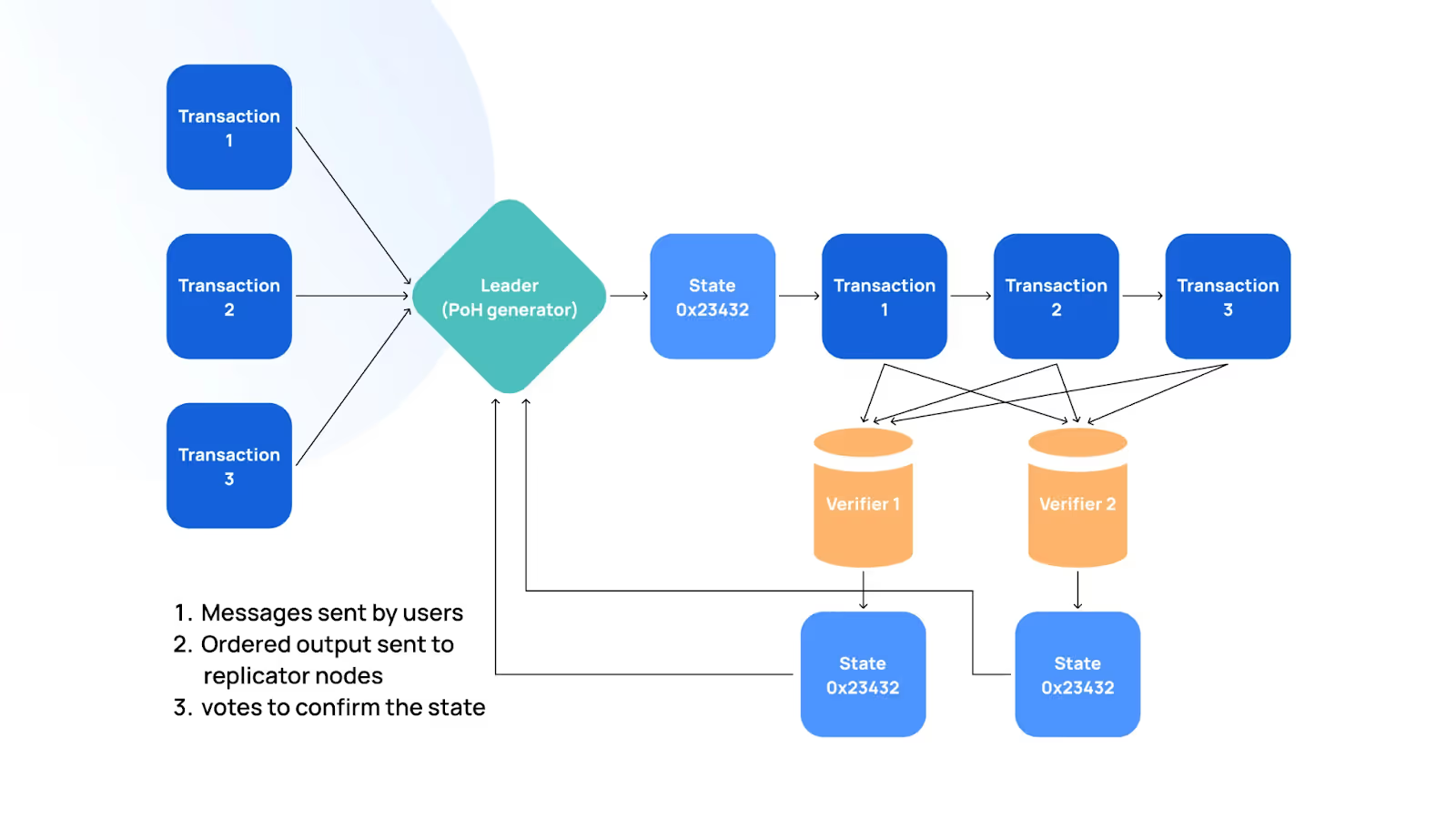
For comprehensive coverage of Solana's transaction lifecycle, fee market mechanics, and priority fee systems underpinning sniper strategies, reference the official Solana documentation.
Organizations dependent on priority access deploy sniping automation: quantitative trading firms pursuing early momentum on token debuts, market makers establishing positions before bid-ask spreads expand, and sophisticated retail operations automating entry timing during volatility spikes.
These organizations pursue three measurable outcomes: reliable first-10 confirmation placement within designated slots, reduced realized slippage during throughput bursts, and fewer capital losses from honeypots or disabled exit functionality.
From an infrastructure engineering perspective (where we excel 😉), these organizations share common requirements:
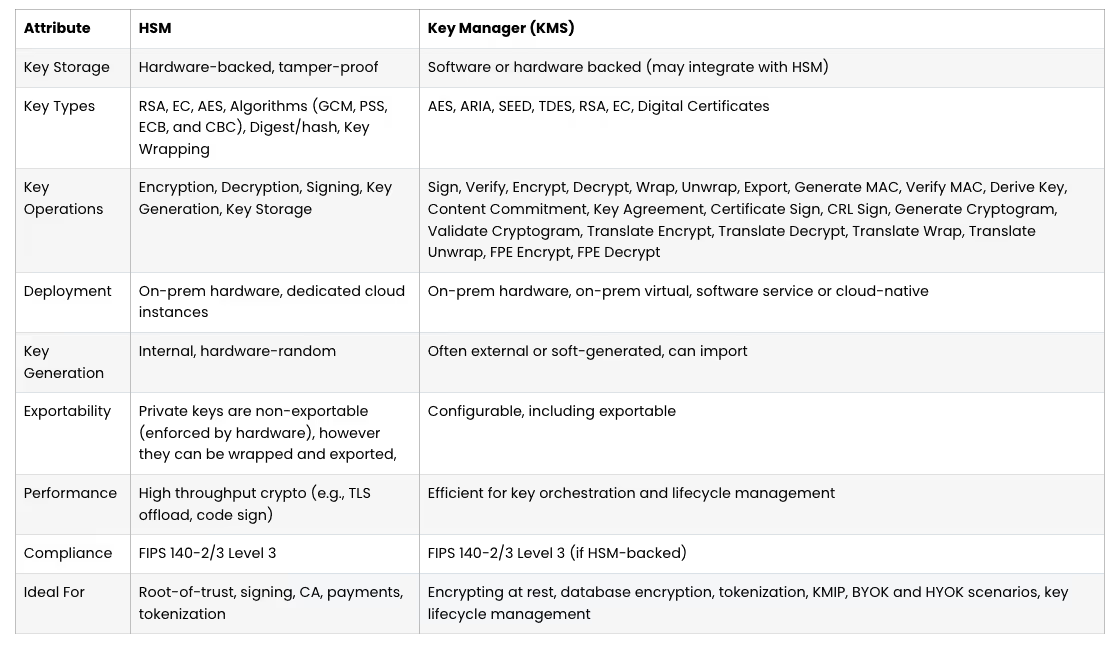
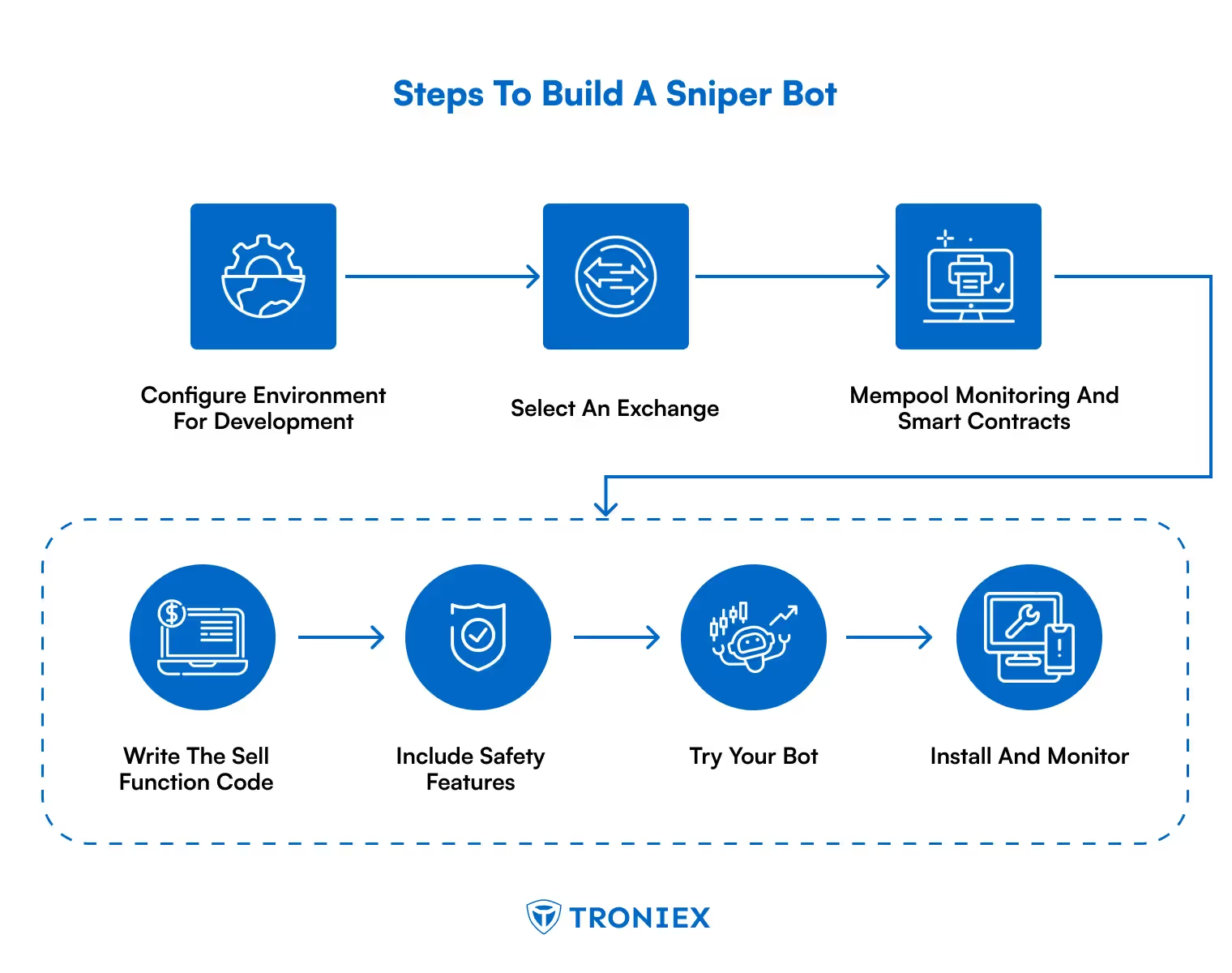
Organizations relying on Solana for launch window liquidity capture, arbitrage execution, or short-duration momentum trading require sniper automation as core infrastructure, not optional tooling.
Raw speed alone doesn't define quality sniping infrastructure. Production systems must demonstrate predictability, governance capabilities, and cost-efficient scalability. Establish service level objectives for both latency and execution success rates, implement circuit breakers triggering strategy suspension at anomaly thresholds, and enforce permission models isolating research environments from production credential access.
Scalability emerges from idempotent transaction builders, exponential backoff retry mechanisms, and isolated key management within secure network perimeters to support 1,000+ daily snipes without credential leakage or spam penalties, deployed on Kubernetes for zero-downtime updates and automatic scaling during volume spikes.
Below we compare Solana bot platforms based on infrastructure capabilities relevant to engineering teams.
| Platform | Interface Type | Core Solana Capabilities (2026) | Security Model | Fee Structure (2026) | Optimal Use Case |
|---|---|---|---|---|---|
| Axiom Trade | Browser-based terminal | Solana-native interface; rapid limit orders and migration snipes; combined perpetuals and yield products; robust analytics; wallet and social feed monitoring. | Non-custodial Axiom wallet with external wallet support; on-chain execution; dedicated trading wallet recommended. | Spot trading ~1.0% with volume-based reductions toward ~0.75%; perpetuals ~0.01% per position (plus network costs). | Organizations seeking unified Solana operations center covering memes, derivatives, and yield with advanced tooling. |
| Trojan Bot (Solana) | Telegram interface + web console | High-speed Solana execution; Trenches new-token monitoring; copy trading functionality; limit and DCA automation; MEV protection with backup systems. | Non-custodial smart-wallet infrastructure (Privy); 2FA and withdrawal controls; segregated Trojan trading wallet recommended. | ~1.0% per execution pre-discounts; substantial fee reductions and referral incentives for high-volume operations. | High-frequency Solana traders operating primarily via Telegram, prioritizing automation, speed, and reward structures. |
| Photon Sol | Browser terminal + analytics | Solana-focused discovery tools; rapid swap interface; instant buy/sell; integrated audit and security flagging; points reward system. | External wallet connectivity (e.g., Phantom); non-custodial; isolated hot wallet recommended for trading operations. | ~1.0% per swap plus standard Solana gas; periodic points promotions can offset transaction costs. | Traders preferring clean browser-based terminal for Solana scanning and rapid execution. |
| GMGN.ai | Web console + Telegram bot | New-token scanning engine; copy trading system; Solana sniping with Anti-MEV configuration; wallet activity tracking; adjustable priority fees. | Non-custodial wallet; Anti-MEV mode requires elevated priority fees; burner wallet usage with conservative position sizing recommended. | Platform fee ~1.0% per successful execution, plus Solana gas and configured priority fees. | Semi-active traders wanting integrated discover → validate → trade/automate workflow. |
| BullX NEO | Web terminal + Telegram (multi-chain) | Solana memecoin sniping with cross-chain support; copy trading system; trending token feeds with terminal interface. | Non-custodial; multiple wallet support; isolated trading wallets recommended over primary holdings. | ~1.0% per Solana execution, with tier- and referral-based discount structures. | Traders operating across Solana and alternative chains requiring solid sniping and copying capabilities. |
| Banana Gun Bot | Telegram bot + Banana Pro web | Multi-chain support including Solana; sniping, limit orders, DCA, copy trading; sophisticated routing and MEV protection; flexible Banana Pro layouts. | Non-custodial bot wallets; wallet creation or import with secure private key storage; fresh wallets funded with limited capital recommended. | Bot/platform fee ~1.0% per executed trade, plus network gas and speed-enhancement tips or bribes. | Advanced traders requiring unified stack across Solana plus EVM/Base, combining Telegram speed with full web terminal. |
| BONKbot | Telegram bot + telemetry web console | One-tap Solana swaps; robust MEV protection modes; rapid execution; portfolio visualization and alerts; telemetry console for deeper analysis. | Non-custodial hardware-wallet-like infrastructure; bot wallet trading; hot wallet risk sizing essential. | Trading fee ~1.0% per execution; portion allocated to BONK buy (partial burn), plus Solana gas and Jito/MEV costs. | Beginners and speed-focused Solana memecoin traders wanting simple Telegram workflow backed by serious infrastructure. |
*Fee structures are indicative and subject to change. Always verify current fee schedules and available rebates/points within each platform or official documentation before deployment.
Platform fees typically range from 0.5 to 1 percent per transaction. Some platforms offer reduced base fees but add fixed per-transaction costs for priority routing through Jito validators. Approximately 0.006 SOL per transaction accumulates rapidly during high-volume periods.
Base fees remain minimal in practice, but priority fees dominate total cost. Individual snipe transactions range from fractions of a cent to several cents in SOL equivalent, depending on network congestion and configured compute unit pricing.
Beyond platform fees, account for implicit operational costs:
Evaluate total cost of ownership, not merely headline percentages. Cheaper bots exhibiting higher revert rates or slower fills often prove more expensive through lost opportunities and wasted fees.
The primary differentiator between amateur snipers and professional trading desks in 2026 is transaction routing methodology:
| Category | Primary Challenges | Solution Approach | Recognized Tools |
|---|---|---|---|
| Ultra-low-latency starters | Failed entries during burst TPS, slippage on token launches, no validator operations | Co-located RPC, priority-fee presets, token filters, anti-honeypot checks, single-node failover. Solid starting snipe bot and snipe bot crypto options for rapid deployment. | Maestro Sniper, Photon Terminal, Sniper, Sol Trading Bot Pro |
| Mempool priority and bundle-aware quantitative | Losing first-confirmation race, reverts at equal fees, MEV exposure | Dynamic priority fees, bundle/preconfirmation paths, slot leader awareness, localized timing. Where “snipe bot crypto” and “front-running snipe bot” searches converge practically. | Helius × Jito bundle flows, Jupiter Sniping + Priority Fees, Birdeye Pro Alerts + custom submitter |
| Strategy-led frameworks | Alpha in logic not raw speed, require CI/testing, multi-signal gating | SDK-first hooks, backtest/paper trade, WebSockets for orderbook/mempool, event-driven execution. DIY crypto sniping bot and snipe bot code paths. | Triton Sniper SDK, TensorSwap SDK, Anchor/TypeScript templates |
| Liquidity-aware and anti-rug specialists | Spoofed liquidity, trap contracts, creator/authority risks | Liquidity thresholds and depth checks, creator/freeze/mint verification, exit-anomaly watchdogs. Safer than generic snipe bots and bot sniper tools. | Rugcheck + Maestro Guardrails, Birdeye Liquidity Gates, SolSniffer |
| Market-making hybrid snipers | Early entry with inventory risk, quote instability in bursts | Immediate post-fill quoting, inventory/RL rules, fee-aware exits. Useful when a coin sniper enters early and stabilizes spread. | Phoenix MM Sniper, OpenBook MM Sniper |
| Managed services with SLOs | No low-latency operations in-house, inconsistent rollouts, weak on-call | 24/7 monitoring/paging, latency SLOs, change control and rollbacks, monthly reviews | Tensor NFT Sniper + MM, Managed Sniping Services, Desk integrations on Helius/Jito with SLAs |

Winning bots combine sub-100ms submission, slot-aware priority fees, and comprehensive pre-trade safety validations. Organize your evaluation by primary needs: speed without validator operations, bundle/priority control for first-confirmation ranking, strategy frameworks for custom logic implementation, or safety-first filtering to prevent loss events during token launches.
Your vendor selection should include proof. Request 7-day reproduction tests covering 100 events with identical RPC and fee configurations. Evaluate P50/P95 submission times, confirmation ranking, revert rates, realized slippage, and time-to-exit on anomaly detection. Require operational fundamentals: multi-RPC failover, clear backoff strategies, per-strategy key isolation, and alerts on confirmation lag. If your team lacks low-latency operational depth, deploy a managed service with SLOs and monthly latency/P&L reviews.
At Dysnix, we architect and deploy production-grade sniper infrastructure on Solana. Whether you're building from scratch or optimizing existing deployments, we provide the DevOps foundation separating profitable operations from expensive experiments.
Our methodology combines Kubernetes-native deployment pipelines, multi-region RPC failover architectures, and real-time observability stacks. We collaborate with RPC Fast to ensure your sniper bots have the low-latency, high-reliability infrastructure required to compete at millisecond precision.
Map your execution path and fee strategies before deployment. Dysnix will benchmark your current infrastructure, optimize priority fee strategies for network conditions, and architect bundle-ready configurations tailored to your trading requirements and risk parameters.
Contact us for an infrastructure review and establish measurable targets for latency, success rate, and operational resilience.