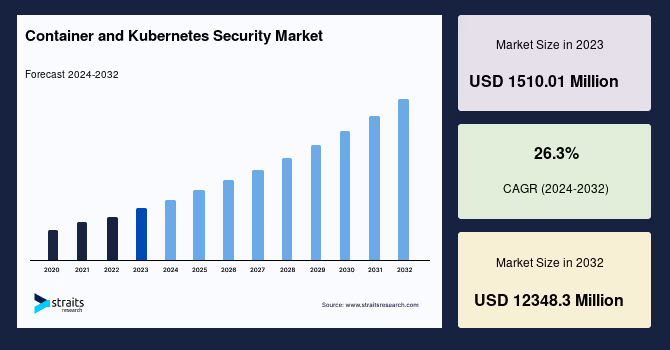
Eighteen minutes. That’s how long, on average, it takes for attackers to probe a new Kubernetes cluster after it goes live, according to the latest Kubernetes Security Report 2025. Just imagine: before your configuration files even settle, bots are already knocking at the door.
The same report shows clusters are getting smarter, leaner, and more secure, with critical vulnerabilities in exposed pods dropping by 50%. Operators are catching up, upgrading faster, and enforcing least privilege. But the arms race is far from over.
And that’s where Kubernetes security companies step in. In 2025, they’re no longer “nice to have.” They’re the shield that stands between your workloads and relentless attack traffic.
Kubernetes security companies are specialized vendors that build tools and services to protect clusters at every layer: the control plane, worker nodes, workloads, and network.
Unlike generic cloud security providers, these companies focus on containerized environments, where risks evolve faster and traditional firewalls or endpoint tools fall short.
Their solutions typically cover four technical domains:
The value of Kubernetes security companies lies not in “extra protection” but in covering attack surfaces unique to Kubernetes: ephemeral pods, dynamic scaling, multi-tenant workloads, and complex RBAC trees. Their tooling bridges the gap between what Kubernetes provides by default and the enterprise-grade defense posture that regulated industries and critical workloads require.
Not every team running Kubernetes needs the same level of protection, but there are clear cases where specialized security vendors become essential.
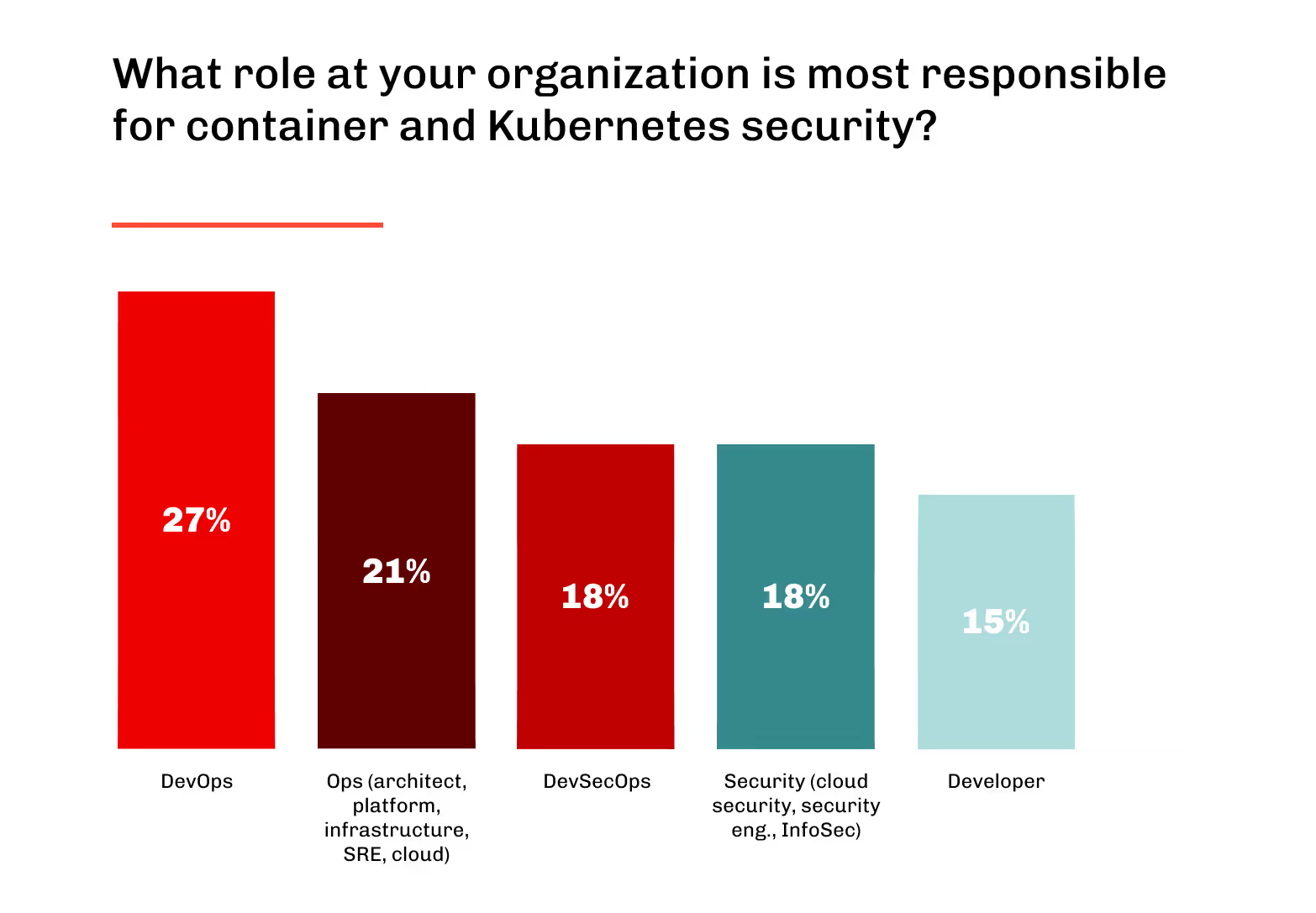
Financial institutions, healthcare providers, and government contractors cannot rely on default Kubernetes settings. They must comply with frameworks like PCI DSS, HIPAA, or FedRAMP, which require continuous vulnerability scanning, auditable access controls, and documented incident response. Kubernetes security platforms deliver these controls out of the box.
Once clusters grow beyond a handful of nodes, manual oversight becomes impossible. Multi-region or multi-cloud deployments with hundreds of services introduce exponential complexity in RBAC, secrets management, and network policies. Security vendors provide centralized dashboards, automated policy enforcement, and runtime anomaly detection across environments.
Public-facing APIs, e-commerce platforms, or SaaS applications hosted on Kubernetes are scanned by bots minutes after deployment. Built-in Kubernetes protections don’t stop credential stuffing, crypto-mining containers, or privilege escalation attempts. Security companies add runtime defense layers with eBPF, syscall monitoring, and container behavior baselines.
In modern CI/CD pipelines, container images pass from developer laptops to production in hours. Without automated scanning, a single unpatched base image can introduce hundreds of CVEs. Kubernetes security vendors integrate directly into GitHub Actions, GitLab CI, or Jenkins, blocking vulnerable images before they reach production.
This year’s leaders include Dysnix, Aqua Security, Palo Alto Networks (Prisma Cloud), Sysdig, SentinelOne, Anchore, Wiz, and Red Hat Advanced Cluster Security.

Together, they define the state of Kubernetes security: advanced runtime monitoring, supply chain validation, zero-trust networking, and compliance automation at enterprise scale.
Dysnix combines deep DevOps expertise with a security-first approach to Kubernetes. Unlike vendors that only offer generic scanning tools, Dysnix engineers perform hands-on Kubernetes penetration testing and deliver end-to-end managed services designed to secure clusters under real production load.
Core strengths:
The typical workflow includes reconnaissance, attack surface mapping, vulnerability exploitation, and detailed reporting with fixes. Instead of just listing CVEs, Dysnix delivers prioritized remediation steps tailored to business goals.
For Explorer Surgical, Dysnix transformed a fragmented cloud architecture into a unified, secure, and auto-scaling Kubernetes environment. The migration eliminated manual monitoring, reduced infrastructure costs by over $20M, and ensured compliance for sensitive healthcare workloads.
With over 100 completed projects and partnerships ranging from fintech to healthcare, Dysnix proves that Kubernetes security is not a product but a service discipline. Their mix of penetration testing, managed services, and architecture optimization makes them one of the few vendors equally effective for startups under rapid growth and enterprises bound by strict compliance.
Aqua Security is a pioneer in cloud-native security with one of the most complete platforms for Kubernetes protection. The company focuses on securing the entire container lifecycle: scanning images in the CI/CD pipeline, enforcing admission policies in Kubernetes, and monitoring workloads in runtime. Their tools detect CVEs, secrets, and malware in container images, generate SBOMs, and validate signatures to prevent supply chain attacks.
In production, Aqua applies eBPF-based monitoring to catch anomalies like crypto-mining, privilege escalation, or unusual network activity. Admission policies integrate with Kubernetes controllers and map directly to CIS Benchmarks and NIST frameworks, giving enterprises compliance-ready enforcement.
Large-scale enterprises, especially in finance and retail, rely on Aqua to protect thousands of workloads across hybrid environments. One client reduced high-severity vulnerabilities by 40% after applying Aqua’s policy-driven controls. Aqua stands out for its ability to combine supply chain integrity and runtime defense in a single platform, making it a strong choice for organizations that need scalable, end-to-end Kubernetes security.
Palo Alto Networks brings Kubernetes security into its broader Prisma Cloud platform, giving enterprises an all-in-one solution for cloud and container protection. The strength of Prisma lies in combining posture management, vulnerability scanning, and runtime defense in a single pane of glass.
What makes Prisma Cloud stand out for Kubernetes security:
Prisma Cloud is often chosen by enterprises already invested in Palo Alto firewalls or network security, as the integration offers a familiar ecosystem and centralized visibility. For global organizations managing multiple clusters across AWS, Azure, and GCP, Prisma delivers consistency and scale.
Sysdig has built its reputation on runtime security for containers and Kubernetes, with a strong open-source backbone through Falco, the CNCF project for threat detection. The company focuses on deep visibility into system calls, container activity, and Kubernetes audit logs, allowing security teams to spot anomalies in real time.
Their platform combines vulnerability management, runtime defense, and compliance. Sysdig scans container images during build, blocks risky deployments with Kubernetes admission controls, and monitors live clusters for attacks such as privilege escalation, crypto-mining, or data exfiltration. Its runtime engine leverages eBPF to capture low-level signals, giving defenders context-rich alerts instead of noisy logs.
Sysdig is widely adopted by enterprises running multi-cloud or hybrid Kubernetes setups, as it delivers a single view of compliance and runtime security across environments. For example, financial and telecom customers use Sysdig to meet PCI DSS and ISO 27001 requirements while handling thousands of workloads. Its tight integration with Falco policies and cloud-native toolchains makes it a go-to choice for teams that need strong runtime protection and detailed forensics.
SentinelOne extends its AI-driven security platform into Kubernetes, focusing on autonomous threat detection and response. Unlike traditional solutions that rely heavily on signatures or static rules, SentinelOne applies machine learning and behavioral analytics to monitor containerized workloads and Kubernetes control planes in real time.
Their approach combines:
SentinelOne is particularly appealing for organizations that value speed of response. Its autonomous capabilities reduce dependence on manual SOC intervention, which is critical when attacks against Kubernetes workloads can unfold within minutes of exposure. Enterprises that already use SentinelOne for endpoint protection often extend it to Kubernetes to achieve unified visibility and detection across endpoints, cloud, and containers.
Anchore focuses on one specific but critical piece of Kubernetes security: container image and supply chain protection. Instead of trying to cover every layer of the stack, Anchore has built a strong reputation for giving DevSecOps teams the tools to ensure that every image running in a cluster is trusted and compliant.
The platform scans container images for vulnerabilities, secrets, and misconfigurations, then enforces policies directly in the CI/CD pipeline. It integrates with tools like Jenkins, GitHub Actions, and GitLab, so vulnerable images never make it into production. Anchore also supports SBOM generation and signature verification, which are increasingly required for compliance frameworks and software supply chain standards.
Large enterprises and government agencies rely on Anchore because of its policy-based enforcement. Security teams can define rules once, such as “no critical CVEs allowed” or “all images must be signed” and enforce them consistently across thousands of workloads. This has made Anchore popular in regulated sectors where supply chain attacks are a top concern.
Wiz has quickly become one of the fastest-growing cloud security companies, and its Kubernetes capabilities reflect that momentum. The platform focuses on cloud security posture management (CSPM) with strong coverage for Kubernetes clusters. It continuously scans configurations, RBAC rules, and workload policies to uncover misconfigurations and excessive permissions that attackers can exploit within minutes of cluster exposure.
A key strength is Wiz’s ability to correlate risks across cloud infrastructure and Kubernetes. For example, it can link a vulnerable container image with an over-privileged service account and an exposed internet-facing load balancer—showing the real attack path instead of isolated alerts. This graph-based analysis makes it easier for security teams to prioritize the few issues that actually matter.
Wiz also integrates Kubernetes findings into broader compliance and governance frameworks, giving enterprises unified visibility across AWS, Azure, GCP, and on-prem environments. Many large enterprises use Wiz to enforce least-privilege policies and meet regulatory requirements such as SOC 2 or HIPAA. In practice, Wiz helps teams shrink their attack surface, catch misconfigurations early, and maintain continuous compliance across thousands of workloads.
Red Hat’s Advanced Cluster Security, born out of the StackRox acquisition, is one of the most Kubernetes-native security solutions on the market. Unlike generic cloud security tools, ACS was built specifically for Kubernetes, with deep hooks into the platform’s control plane, admission controllers, and policy engines.
The platform focuses on three key areas: vulnerability management, compliance, and runtime defense. It scans container images and Kubernetes resources for CVEs and misconfigurations, enforces PodSecurity and RBAC best practices, and continuously monitors running workloads for anomalous behavior. Integration with Open Policy Agent (OPA) and Kubernetes-native APIs makes enforcement seamless across hybrid and multi-cloud clusters.
Red Hat ACS is widely used by enterprises that already rely on OpenShift, but it works across any CNCF-compliant Kubernetes distribution. Customers choose it for its tight integration, compliance-ready reporting, and ability to scale across dozens of clusters. For regulated industries, it helps demonstrate adherence to frameworks like NIST 800-53 or SOC 2 without bolting on external tooling.
The table below highlights the most important characteristics to compare when evaluating providers.
| Criterion | What to Look For | Why It Matters |
|---|---|---|
| Scope of protection | Coverage across build, deploy, and runtime phases | Ensures no blind spots in CI/CD, cluster configs, or live workloads |
| Policy enforcement | Kubernetes-native controls (OPA, Gatekeeper, Pod Security, RBAC management) | Prevents risky deployments before they reach production |
| Runtime defense | eBPF-based anomaly detection, syscall monitoring, automated response | Protects against zero-day exploits and crypto-mining attacks in real time |
| Supply chain security | Image scanning, SBOM generation, signature verification | Stops vulnerable or malicious images from entering clusters |
| Compliance support | CIS Benchmarks, PCI DSS, HIPAA, SOC 2, FedRAMP reporting | Reduces audit burden and helps meet industry or regulatory standards |
| Integration | Compatibility with CI/CD (Jenkins, GitHub, GitLab), cloud providers, service mesh | Simplifies adoption and avoids tool sprawl |
| Scalability | Proven performance in multi-cluster, hybrid, or multi-cloud setups | Keeps costs predictable as infrastructure grows |
| Ease of use | Centralized dashboards, actionable alerts, automation | Helps DevOps and SecOps teams collaborate without drowning in false positives |
| Vendor expertise | Proven case studies, industry-specific solutions, enterprise support | Increases trust and ensures practical security outcomes, not just tooling |
Kubernetes has become the backbone of modern infrastructure, but that also makes it a prime target. Reports from 2025 show how quickly attackers probe fresh clusters, often in under 20 minutes, and how costly misconfigurations can be if left unchecked. The right security company doesn’t just reduce risks, it enables teams to innovate faster without the fear of breaches or compliance failures hanging over every deployment.
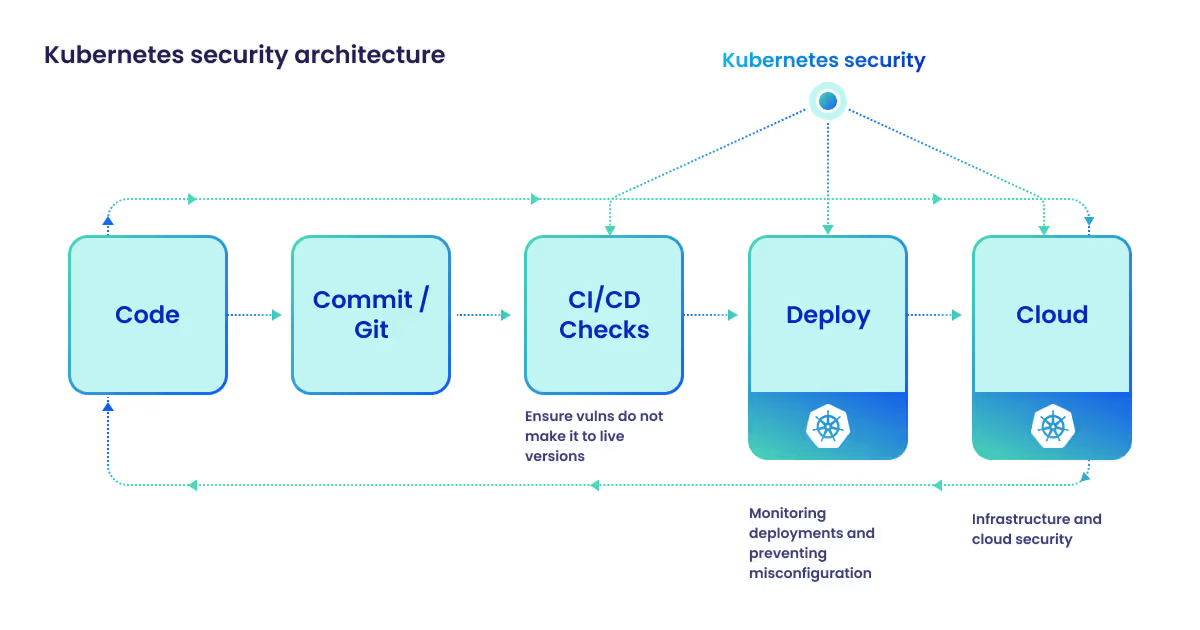
In this fast-changing landscape, Dysnix takes a different approach. Instead of offering only off-the-shelf tooling, we embed directly into your Kubernetes lifecycle: running penetration tests that simulate real attacks, hardening your cluster architecture to industry standards, and operating managed services that keep workloads secure around the clock. It’s practice shaped by healthcare, fintech, and SaaS cases where uptime and compliance meant everything.
“We don’t believe in generic dashboards. We believe in testing your defenses the way attackers would and then making sure your cluster can handle it.”
— Dysnix